How to Enable Exploit Protection from Windows Defender in Windows 10. Even Users apply various security features to protect their windows 10 system. Windows 10 Exploit protection is one of them. It is an important security feature of Windows 10 that included in Windows defender security settings. Windows defender exploit protection defends your system against malware attacks as well as viruses. It is very easy to find exploit protection feature in windows 20. You can find it from Windows security under Settings App.
How to Enable Exploit Protection from Windows Defender in Windows 10
To get advantages and protect your system from external threats, you must enable Windows defender exploit protection feature in Windows 10. To enable it, follow these steps: –
- Press Win + I shortcut key.
- Windows settings app will open.
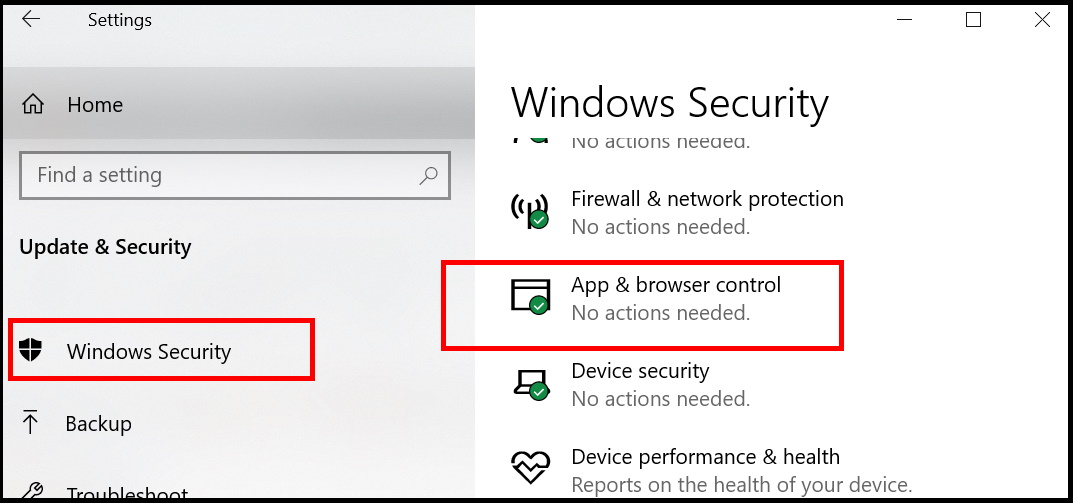
- Thereafter choose the option Update & Security.
- Now from the left pane, select the option Windows Security.
- Thereafter choose the option App & Browser control from the right pane of settings window.
- Thereafter select the option Exploit protection settings under App & browser control page.
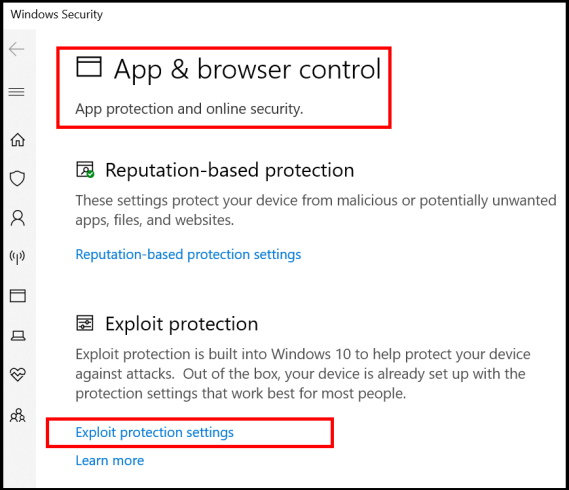
- Now Exploit protection settings page will open.
- Then go to the system settings as well as Program settings option.
- Thereafter turn all settings in default On mode in Each settings mitigation.
Exploit Protection Mitigations Settings
You can set each of the mitigations on, off, or to their default value. Some mitigations have additional options also.
1. Control flow guard (CFG)
It ensures control flow integrity for indirect calls. You can optionally suppress exports and use strict Control Flow Guard. This feature applied to System and app-level.
2. Data Execution Prevention (DEP)
This feature prevents code from being run from “data-only memory pages” such as the heap and stacks. It is configurable only for 32-bit (x86) apps and permanently enabled for all other architectures. You can optionally enable ATL thunk emulation. This feature applied to System and app-level.
3. Force randomization for images (Mandatory ASLR)
This feature forcibly relocates images which not compiled with /DYNAMICBASE. It can optionally fail in loading images that don’t have relocation information. This feature applied to System and app-level.
4. Randomize memory allocations (Bottom-Up ASLR)
It randomizes locations for virtual memory allocations as well as includes system structure heaps, stacks, TEBs, and PEBs. You can optionally use a wider randomization variance for 64-bit processes.
5. Validate exception chains (SEHOP)
It ensures the integrity of an exception chain during exception dispatch. it is configurable only for 32-bit (x86) applications.
6. Arbitrary code guard (ACG)
It prevents the introduction of non-image-backed executable code and prevents code pages from being modified. You can optionally allow thread opt-out. This feature also allow remote downgrade (configurable only with PowerShell).
People also Search for: –
- Windows 10 exploit protection override
- Windows 10 exploit protection performance
- What is exploit protection
- Windows defender exploit guard
- Exploit protection program setting
- Exploit protection system setting
- Disable windows defender exploit protection
That’s all.
